If you think your social media or email account has been hacked, wrestle it away from the bad guys by acting fast.
Hackers use a bunch of different tactics to try to compromise people’s email, banking, social media, device, and other online accounts. Sometimes they do this to spam your friends with coupons, but other times they want to steal your money or identity. By alerting authorities and following a few steps, you can often retake control of your hacked account.
However, fast action is crucial. If you suspect that your digital account has been hacked, do something about it as soon as you can. Here’s what you need to know right now!
How does an account get hacked?
Security breaches happen in many ways – sometimes you might click on a bad link, or the company in charge of the account could be attacked. This is why cybersecurity is so important to us all, and why we at the National Cybersecurity Alliance are so hyped up about it!
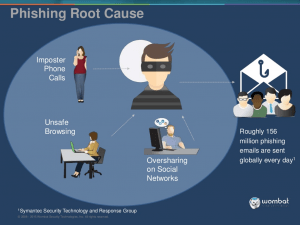
Commonly, an account is hacked through phishing. This is when cybercriminals use misleading emails, social media posts, phone calls, texts, or DMs that lure you to click on a bad link or download a malicious attachment. If you take the bait, the hackers can get access to your device or account.
Another common way your account could be hacked is if there is a data breach that reveals your username and password. The company controlling the account in question could be hacked, for example. If you reuse passwords, if any platform you use is compromised then cybercriminals might know your password for many accounts. This is why you should have a unique password for each account and change your password ASAP if you find out a platform you use has had a breach.
Signs your account has been hacked
Does something seem off about one or more of your online accounts? Know the common symptoms of a hacked account.
- Unusual Social Media Activity: Your social media profile publishes posts that you didn’t create. Ditto for direct messages – hackers might use your account to send phishing DMs or posts to your followers. Often these posts encourage your friends to click on a link, download an app, or buy something through an online store.
- Unexpected Messages to Friends: Friends and followers tell you that they received emails from your email address that you never sent, or DMs through social media that you never authored.
- Unauthorized Login Notification: A company tells you that your information was lost via a data breach. In many places around the world, companies are required by law to tell you if they lost your data in a breach or cyber attack.
What are 4 things to do when your account is hacked?
If you think an account is hacked, snap into action, and take a few quick steps to staunch the damage. You have the power to give cybercriminals the boot!
- Change Your Password: This will likely lock out the hacker. Unfortunately, it can also work the other way around: the hacker might change the password and lock you out. In this case, try using the “forgot my password” function to reset it. If that doesn’t work, contact the platform ASAP. If you used the same password for other accounts, you should change all of them, and start using unique passwords for every account. Use a password manager to generate and store all your passwords.
- Notify your contacts: That your account was hacked. Let them know they may receive spam messages that look like you sent them. Tell your contacts they shouldn’t open these messages or click on any links contained in them. When the situation is cleared up, let everyone know that your accounts are secure again.
- Update Your Security Software: Make sure your security software is up to date. Scan your system for malware, especially if you suspect your computer might be infected with a virus. Antivirus software will scan your device to check for any security issues.
- Seek Assistance: Contact people who can help you. If you suspect someone has stolen money, this might mean calling the police and your bank. If a work account was breached, let your IT department know. If a social media or email account was hacked, alert the platform, and seek their help. If you think someone has stolen your identity, it is worth contacting the FTC. Let trusted friends and family know what you are going through so they can on the lookout for weird messages or posts from your account.
Resources
Here’s where to turn if you have an account with one of these popular websites and you think its been hacked:
Source: National Cybersecurity Alliance https://staysafeonline.org/online-safety-privacy-basics/hacked-accounts
 This post is presented by the GW IT Cybersecurity Risk and Assurance team.
This post is presented by the GW IT Cybersecurity Risk and Assurance team.
#SecuringGW is a shared responsibility, so if you see something, say something. Report suspicious digital activities, including phishing emails, to abuse[@]gwu.edu.
IT Support Questions? For IT support, please contact the Information Technology Support Center at 202-994-GWIT (4948), ithelp[@]gwu.edu, or visit ithelp.gwu.edu.