We get this question a lot. You're surfing the web and you click a link and all of the sudden, you see this screen:
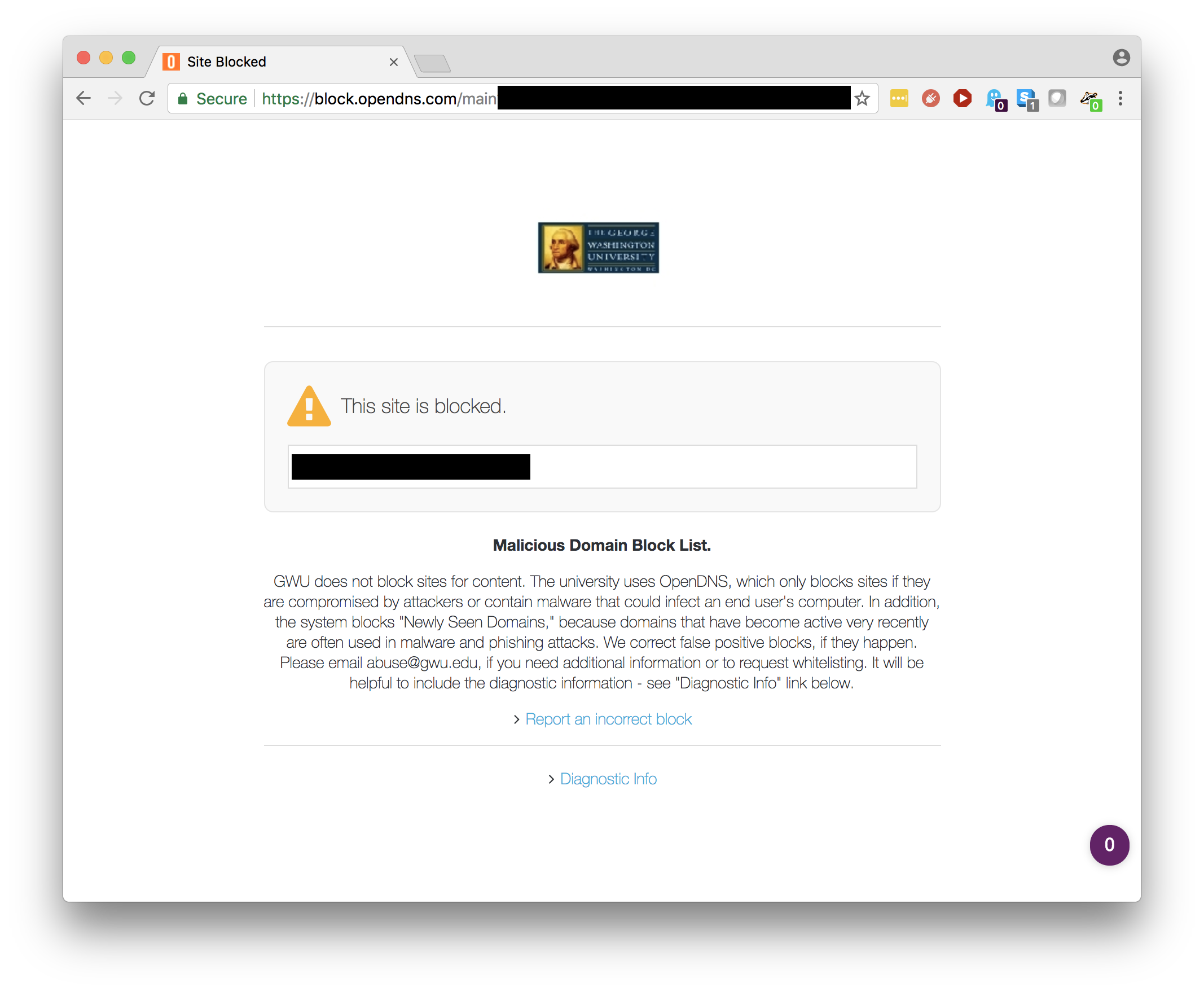
We understand that this can be frustrating, especially when you believe that the website in question is completely safe and legitimate. The GW Security team is happy to correct any incorrect blocks and encourage you to contact us using the form provided on the block page. We also want to take this opportunity to provide an overview as to why some websites get blocked and what you can do.
The GW network is set up to use domain resolution services provided by Cisco OpenDNS Umbrella. OpenDNS serves over 65 million users daily and provides timely protection against an ever growing array of threats.
Before we talk about blocked sites, we want to mention a few categories that are commonly mentioned in block complaints and want to confirm that we do not block the following categories:
- Controversial (for political, lifestyle or any reason) sites
- Pornography (except illegal)
- Gaming
- Coin mining (except for domains implicated in unsolicited browser coin mining and seen used by coin stealing / mining malware)
- Video streaming / sharing / downloads
You can read OpenDNS anti-censorship policy here: https://www.opendns.com/about/anti-censorship-policy/
That said, pornography, gaming, coin mining, and (illegal) video sharing or streaming sites have higher than normal percentage of compromised and malicious / malvertising (ads redirecting to malware and adware) sites that could be blocked.
We also strongly advise against running gaming or coin mining servers on the GW network as they are often a target of various types of cyberattacks, including DDoS, and could be flagged for inappropriate use of GW resources such as electricity and shared bandwidth.
Here are some reasons why a website you're trying to visit may be blocked:
Reason #1. This is not the site you intended to visit.
We block a lot of malicious and malvertising (ads redirecting to malware and adware) sites. Sometimes legitimate and clean websites could have an advertising pop up or redirect that gets blocked, thus giving an impression that the site you are visiting is blocked as well.
Double check the URL. You may be trying to visit a similar, likely malicious, website that is blocked (e.g. gwu.com vs. gwu.edu)
What to do:
Check the URL shown in the block page. If this is not the URL you typed or expected, try your original destination URL or check for other open tabs in your browser where the site you visited may still be open.
Reason #2. Malware, Adware, Scareware, Scams, Phishing, Bad hosting.
This category is obvious but still requires a few notes. Imagine your hometown restaurant site gets blocked and you believe it is wrong because you visited that site many times before so it seemed clean. There are a few reasons why blocks of legitimate sites may occur:
- The site might actually be compromised. It does not have to be infecting visitors, but it could be detected as having phishing links, browser coin mining code, or malicious code redirecting visitors to suspicious sites.
- Collateral damage from bad sites using the same hosting server. Sometimes OpenDNS services block IP addresses that are home to multiple malicious domains.
- The site was compromised in the past but is clean now. However, some security providers may still have it blacklisted. Usually blocklists are shared between companies.
- False positive blocks by some security providers may affect the overall score.
- Human errors - non-malicious websites that were mistakenly blocked as part of an incident response investigation.
What to do:
If you believe it is wrong, fill in the form on the block page and we will reply promptly and whitelist or unblock clean sites.
Reason #3 Newly seen domains.
Newly seen (by OpenDNS) domains are temporarily blocked.
New domains are often registered in the thousands as a new malware campaign effort to bypass blocks on the sites that have already been flagged as malicious. The Newly Seen Domains (NSD) is a security category that works by checking OpenDNS logs to see lookups for that domain that were not seen across all OpenDNS global sensors in the past. If they see a lookup for that new domain, it is flagged as “newly seen” and added to the NSD list. This temporary block will eventually expire. The expiry time depends on the characteristics of the parent domain or the IP space / registrant. Typically domains stay in the list between one to three days, but it isn't fixed to a set period of time. During that time malicious domains often get added to the appropriate security category and benign domains will become unblocked.
A significant portion of the domains that are categorized as newly seen will not, in fact, be malicious and OpenDNS takes precautions against blocking content delivery networks (CDN) known to generate a lot of new subdomains as well as other well known benign providers.
Please note that the first query to the domain will be allowed, because if OpenDNS has never seen it, it was not yet added to the Newly Seen Domain Category. The time gap between when a domain is first queried and before it appears in the list of domains matching the Newly Seen category is ?????
Important note: A domain will enter the process to be flagged as newly seen not when it is first registered, but rather when it is sampled in a DNS query to OpenDNS Umbrella resolvers - in other words, when a visit is attempted. Not every DNS query to Umbrella is sampled, and therefore some very low traffic domains may not be flagged as newly seen immediately.
What to do:
Fill in the form on the block page; we will reply promptly and whitelist it so you do not have to wait for the Newly Seen Domain block to expire in a few days.