Cybersecurity has become one of the most significant hot topics inside and outside technology circles over the last two years. From securing learning devices due to a rise in digital learning during the COVID-19 pandemic to coping with the fallout of high-profile breaches of national infrastructure such as the Colonial Pipeline, there is an evidently constant news cycle dedicated to cybersecurity mishaps and concerns. With this continuous stream of bad news, it can be challenging for you to know how to keep secure in the face of cybersecurity and threat actors.
Everyday users have a huge role in cybersecurity threat prevention, detection, and remediation. According to a Wall Street Journal article, many hacks are successful by convincing someone inside or close to the target company to divulge network access credentials or other critical information. Therefore, GW’s first line of defense in helping to combat cyber-related issues is you.
Here are 4 essential best practices that you can adopt today to enhance your cybersecurity and create a more secure cyberspace for you and GW.
Watch out for Phishing Attempts
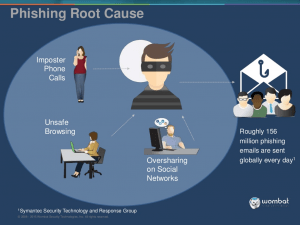
Phishing is when a threat actor poses as a legitimate party such as a bank, delivery service or other organization in an attempt to get individuals to click harmful links. Phishing remains one of the most popular tactics used today. In fact, 80% of cybersecurity incidents stem from a phishing attempt. While phishing has gotten more sophisticated, the phishing signs remain the same. Look for typos, poor graphics, and other suspicious characteristics (incorrect logo or email address) as these can be red flags indicating that the content is a phish. In addition, if you think you have spotted a phishing attempt while logged into the GW network, report the incident to GW IT immediately. To report an incident please contact the GW Information Technology Support Center at 202-994-GWIT (4948) or email abuse@gwu.edu .
Update your Password
Password cracking is another tactic that cybercriminals use to access sensitive personal information. To guard against password cracking, having unique, long and complex passwords is one of the best ways to boost your cybersecurity immediately. It is highly recommended not to repeat passwords across your accounts because once a hacker cracks one account, they can easily do the same across all of your accounts.
Passwords can be tough to remember. That’s why it’s smart to use a password manager to help you secure your various passwords in one place. Password managers are easy to use and can automatically plug-in your stored password when you visit a site. Along with other security tips, password managers minimize the risk of mis-managing account passwords.
Take Advantage of Secure Wi-Fi
Mobile hotspots and public Wi-Fi networks are typically not password-protected, so it’s easier for threat actors to gain unauthorized access to devices. Students, faculty, and staff should take full advantage of the university Wi-Fi networks when on campus. They are password-protected and only allow internet access across the university premises, operating as a secure online bubble for every user to work in peace.
Lock your Device
Whenever you're logged into your devices (computer, laptop, phone, etc.), you’re also open to potential unauthorized access by hackers and other threat actors. The easiest way to prevent unauthorized access to your device is to lock it whenever you leave it unattended. All you have to do to get back on your device is enter the correct password, and you can pick up where you left off. If you wouldn't leave your house with the front door wide open, you should not leave your devices unlocked, especially when they are unattended.
This blogpost is offered to you by the GW Information Security and Risk Services team. For more information on GW IT Security, please visit our security website: https://it.gwu.edu/gw-information-security
#SecuringGW is a shared responsibility, so if you see something, say something. Report suspicious digital activities, including phishing emails, to abuse@gwu.edu.
IT Support Questions? For IT support, please contact the Information Technology Support Center at 202-994-GWIT (4948), ithelp@gwu.edu, or visit ithelp.gwu.edu.
Original blog content provided by The National Cyber Security Alliance www.stayfaeonline.org, modified and posted with permission.