We frequently hear about cyber-attacks on organizations using highly technical and sophisticated methods, involving malware and vulnerabilities that most people don’t understand. However, what we don’t typically hear about is how the attacker got in. According to Verizon’s Data Breach Investigation Report, in 2019, a third of all data breaches involved social engineering attacks to include phishing, pretexting, and a variety of other social engineering methods.
Social Engineering involves gaining the trust of unsuspecting users via manipulation or trickery, in order to gain unauthorized system access, credentials, or commit fraud. Attackers will attempt to take advantage of a multitude of psychological traits such as carelessness, curiosity, empathy, complacency, and most frequently ignorance.
Why does it Matter?
Social Engineering attacks are more common than you might think and odds are that you will encounter one yourself in some form or another. Failing to recognize a social engineering attack could range from a minor inconvenience to a life changing event. Compromise from such an attack could lead to needing a password reset to having a bank account drained of funds, or could even be the launching point for the next massive data breach that makes headlines worldwide.
For example, the 2020 Twitter hack, which affected numerous high-profile accounts, resulted from a social engineering attack targeting employees. Similarly, the 2020 SolarWinds breach, one of the most significant cyber-espionage campaigns, involved social engineering tactics used against employees to gain access to critical infrastructure.
Social Engineering is a large threat to the safety of not just large organizations, but also the individual.
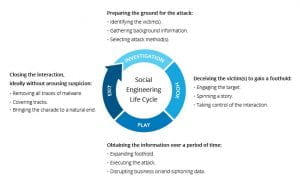
Social Engineering Life Cycle
Much like software development and risk management, many cyber-attacks follow a lifecycle approach; with a continuing cycle of input and output constantly improving the process. Social engineering is no different and even has a few lifecycle models dedicated to it. In its simplest form however, the Social engineering lifecycle follows four basic phases: Investigation, Hook, Play, and Exit.
The Investigation phase is when an attacker performs their recon. They might choose their targets based on position within an organization, ease of access, or they might choose a wide range of targets just to see what sticks. After choosing a target they will use public information to learn as much as possible. Sources such as social media, company websites, and other profiles provide a wealth of information for attackers to use.
The Hook phase involves the initial interaction with the target; ranging from email to in person contact. During the hook, the attackers focus is on spinning a web of lies to manipulate victims at their will.
During the Play phase an attacker gains a stronger foothold and carries out the attack. Depending on their goals, they will begin disrupting or stealing sensitive and valuable data.
The Exit phase points to the end of the lifecycle. The Social Engineer will attempt to remove all traces of their presence and bring an end to their charade. Everything the attacker has gained or learned during the process is then used during a new attack cycle to more effectively con another victim.
Social Engineering and unaware users provide a vast attack surface that can be easily taken advantage of. Meaning that you need to do everything you can to be prepared for and protect yourself from the conmen of the internet age.