Devices such as cell phones, laptops, tablets are increasingly relied on whether from home, campus, and workplaces. The interconnectivity of those devices, especially from home locations, was heightened during the pandemic lockdown. According to recent data, smart home systems are set to rise to a market value of $157 billion by 2023, and the number of installed connected devices in the home is expected to increase by a staggering 70% by 2025. With the rise in virtual work and learning, it’s critical that you remain vigilant in practicing smart cyber hygiene while online. Here are some useful tips:
Smart Devices need Smart Security
Make cybersecurity a priority when purchasing a new cell phone, laptop, or tablet device. When setting up your new device, be sure to set your privacy and security settings, bearing in mind that you can limit with whom you are sharing information. Once your device is set up, remember to keep tabs on securing the information and where it is stored. Make sure that you manage location services actively to avoid unwittingly exposing your location.
Put Cybersecurity First
Make cybersecurity a priority when you're connected and online. Some precautions with all of your online accounts include performing regular software updates, downloading and installing software from trusted sources, using Two Factor Authentication (like we have at GW), and avoid being phished by ensuring that you know senders of an email before opening attachments.
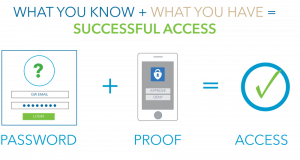
Make passwords and passphrases long and strong
Generic and easy-to-remember passwords are easy to hack. Create secure and strong passwords, and be sure to combine capital and lowercase letters with numbers and symbols. At a minimum, change your passwords every 6-months. If you need help remembering and storing your passwords, use a trusted password manager.
Avoid connecting to public WiFi
As smaller and more capable devices enable us to be mobile, we are all tempted to change scenery and change our physical location like a coffee shop or another type of public space. When you are away from trusted networks (your home or GW, for example), be wary of free, no password required, and even corporate hotspots. These connections may be fraudulent and easily accessible by bad actors.
Use caution with publicly shared computers
Avoid using publicly shared computers as often as possible. If you do use these, be careful and thoughtful in the information you share while online. If you are using your own devices, use known network hotspots, consider using your cellular connection (phone tethering), and avoid performing sensitive activities like accessing banking online.
Turn off WiFi and Bluetooth when unneeded
The uncomfortable truth is, when your WiFi and Bluetooth are on, they usually are set up to broadcast availability/presence and effectively invite other devices to connect. While not always practical, to stay as safe as possible, switch them off if you do not need them. It’s a simple step that can help alleviate tracking concerns and incidents. You can also secure your WiFi and Bluetooth connections through your device settings.
Staying safe online is an active 24/7 process that requires constant oversight 365 days a year. These helpful steps are how we in GW IT do our part to help you in doing your part to remain cyber smart.
For more information on GW IT Security, please visit our security website: https://it.gwu.edu/gw-information-security.
IT Support Questions? For IT support, please contact the Information Technology Support Center at 202-994-GWIT (4948), ithelp@gwu.edu or it.gwu.edu. For self-help resources and answers to frequently asked questions, please visit the GWiz knowledge base at http://go.gwu.edu/GWiz.
Original blog content provided by The National Cyber Security Alliance www.stayfaeonline.org, modified and posted with permission.